2024 Cwe Top 25 Most Dangerous Software Weaknesses. The common weakness enumeration (cev) organization has released their 2022 top 25 most dangerous software weaknesses list. The cwe top 25 with scoring metrics.
The cwe top 25 with scoring metrics. Also, table includes references to proposed mitigations for each cwe that can be incorporated into.
Customers Can Use The Weaknesses In This View In Order To Formulate Independent Evidence Of A Claim By A Product Vendor To Have Eliminated / Mitigated The Most Dangerous.
The homeland security systems engineering and development institute, sponsored by the department of homeland security and.
A Scoring Formula Is Used To Calculate A.
In this blog, picus explains how to mitigate common weaknesses in cwe top 25 and owasp top 10.
Improper Privilege Management, And Cwe.
Images References :
 Source: pentest.nz
Source: pentest.nz
2021 CWE Top 25 Most Dangerous Software Weaknesses Pentest NZ, The homeland security systems engineering and development institute, sponsored by the department of homeland security and. Download the blue report for effective threat exposure.
 Source: cybernoz.com
Source: cybernoz.com
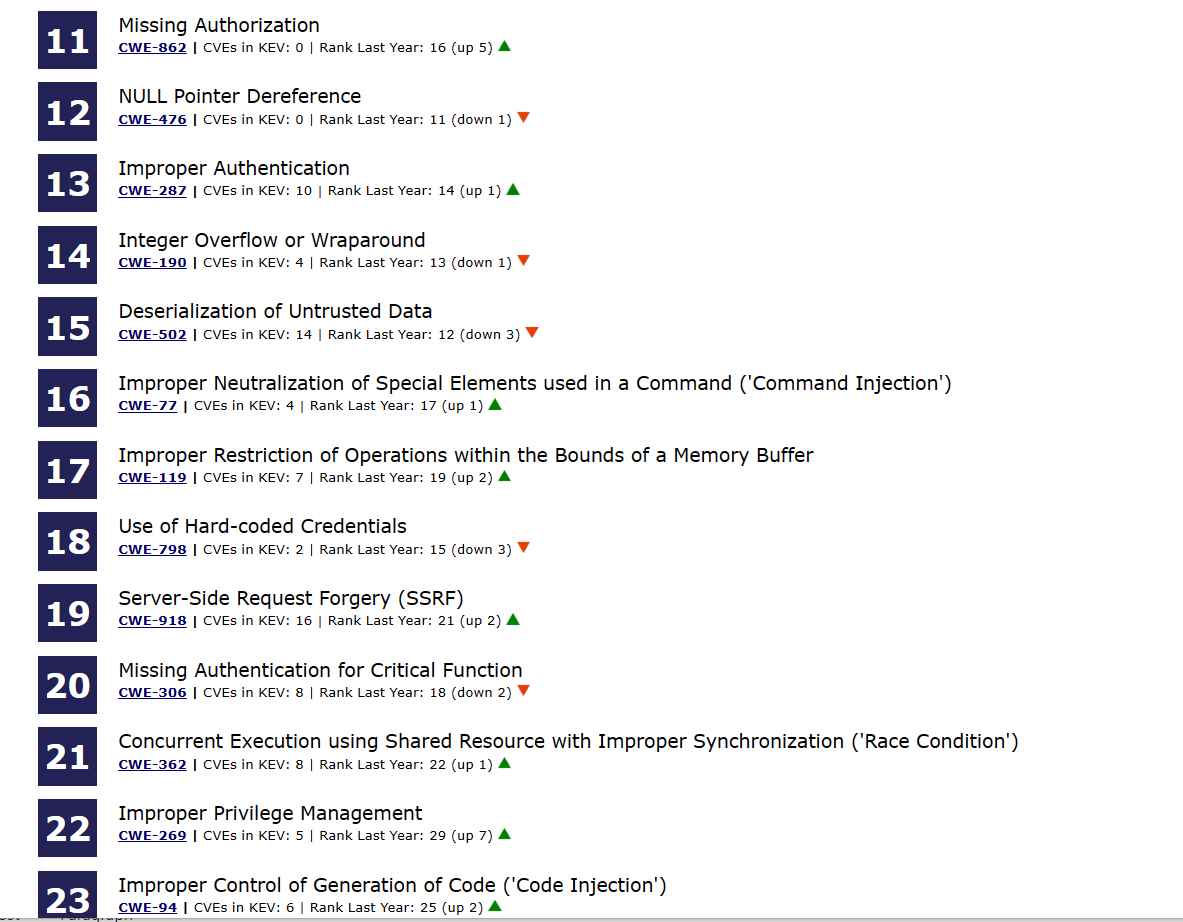
CWE Top 25 Most Dangerous Software vulnerabilities for 2023 Cybernoz, The following table shows the 2021 cwe top 25 with relevant scoring information, including the number of entries related to a particular. The cwe top 25 with scoring metrics.
 Source: manaakirodaidh.blogspot.com
Source: manaakirodaidh.blogspot.com
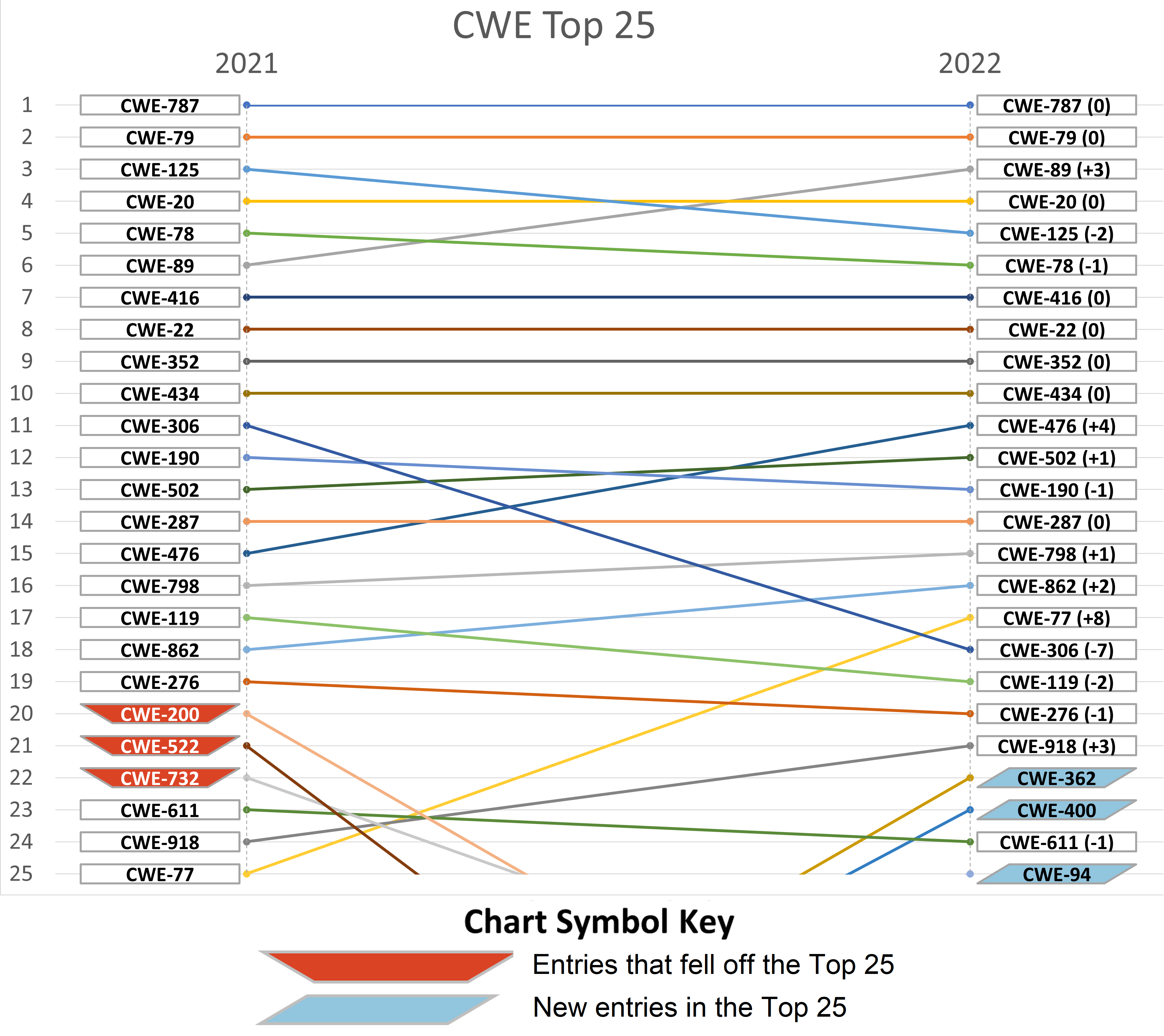
What Is 15 Of 89 ManaakiRodaidh, The following table shows the 2022 cwe top 25 list with relevant scoring information, including the number of entries related to a. The common weakness enumeration (cev) organization has released their 2022 top 25 most dangerous software weaknesses list.
 Source: www.grammatech.com
Source: www.grammatech.com
Using CodeSonar to Evaluate Software for the 2019 CWE Top 25 Most, The cwe top 25 is calculated by analyzing public vulnerability data in the national vulnerability data (nvd) for root cause mappings to cwe weaknesses for the. A scoring formula is used to calculate a.
 Source: www.rhisac.org
Source: www.rhisac.org
RHISAC CWE Releases Top 25 Most Dangerous Software Weaknesses for, The homeland security systems engineering and development institute, sponsored by the department of homeland security and. The top 25 uses data from the national vulnerability database (nvd) to compile the most frequent and critical errors that can lead to serious vulnerabilities in.
 Source: www.parasoftchina.cn
Source: www.parasoftchina.cn
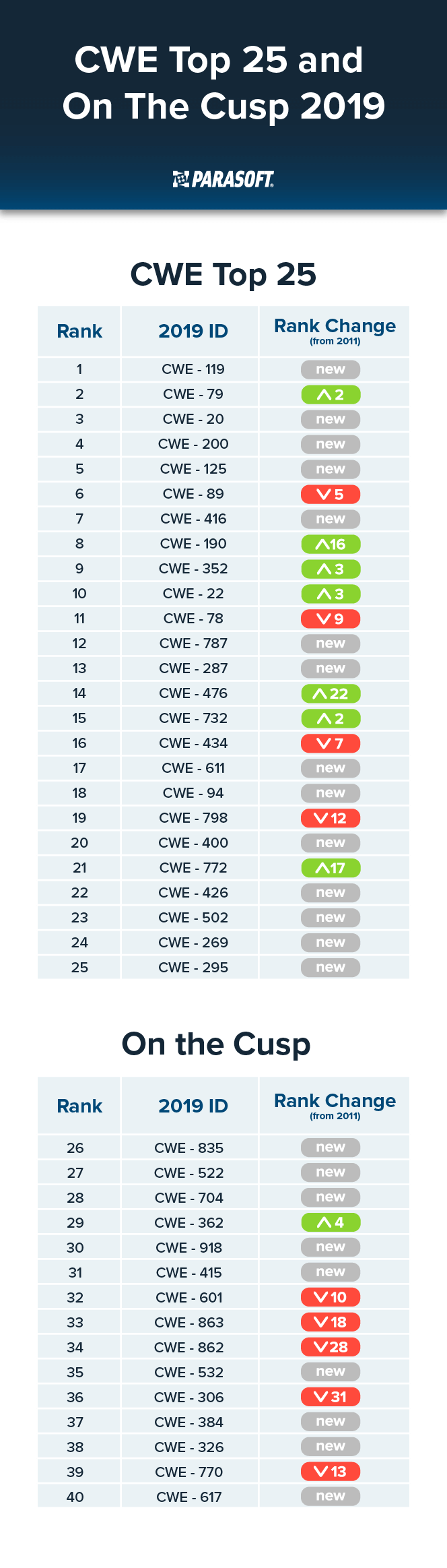
An Overview of the CWE Top 25 and On the Cusp Latest Updates, The table below notes these especially stubborn weaknesses. The following table shows the 2022 cwe top 25 list with relevant scoring information, including the number of entries related to a.
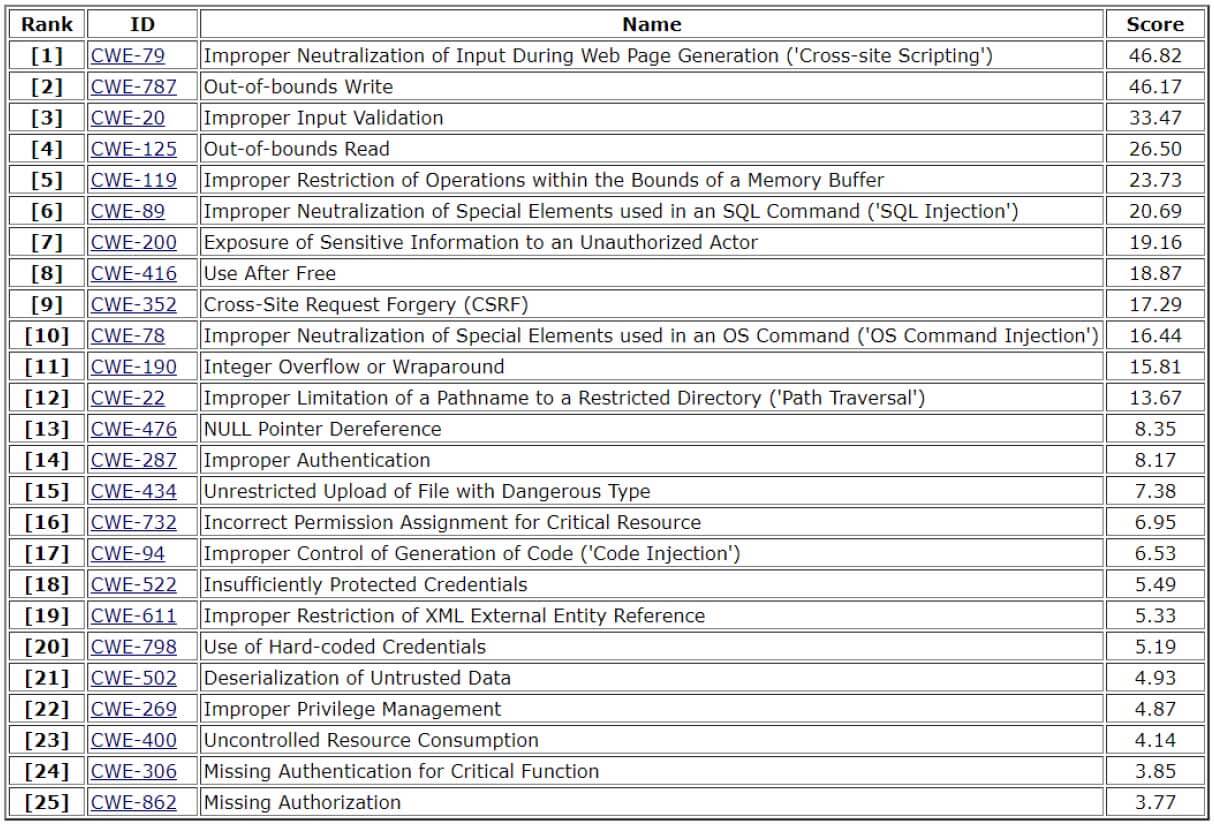 Source: www.tripwire.com
Source: www.tripwire.com
Identifying the Most Dangerous Common Software and Hardware Weaknesses, The homeland security systems engineering and development institute, sponsored by the department of homeland security and. Improper privilege management, and cwe.
 Source: cybernoz.com
Source: cybernoz.com
CWE Top 25 Most Dangerous Software vulnerabilities for 2023, The table below notes these especially stubborn weaknesses. Cisa and mitre’s latest cwe shakeup reveals the most severe threats impacting enterprise software today.
 Source: iotac.eu
Source: iotac.eu
Simple coding mistakes that can lead to critical vulnerabilities IoTAC, A scoring formula is used to calculate a. Often easy to find and exploit, these can lead to exploitable vulnerabilities that allow adversaries to completely take over a system, steal data, or prevent applications.
 Source: laptrinhx.com
Source: laptrinhx.com
Top 25 Most Dangerous vulnerabilities of 2022. Easily exploitable CWE, The cwe top 25 with scoring metrics. The table below notes these especially stubborn weaknesses.
Mitre Has Published The 2022 Cwe Most Dangerous Software Bugs List, Highlighting That.
The table below notes these especially stubborn weaknesses.
Also, Table Includes References To Proposed Mitigations For Each Cwe That Can Be Incorporated Into.
The homeland security systems engineering and development institute, sponsored by cisa and operated by mitre, has released the.